So I went to a CTF event with my friends. It was really an awesome experience and the challenge was pretty interesting. Unlike any other CTFs, this one had only one challenge and that’s it, we had 24 hours to get the flag!
It was actually an individual CTF but you know the deal, as we went as a team, we played as a team 😅. The CTF consisted of web exploitation, steganography, cryptography, and pwning.
But what does a CTF has to do about this tool? Well, here we go. We were solving the challenge steadily and were really happy about it! But at one point we just got stuck, it was a cipher and we weren’t able to get what type of encoding/cipher it was for literal hours! One thing was that we were not really experienced with crypto as we only focused on web, pwn, binary exploitation, and all that good stuff!
It was Base91, we didn’t expect such a cipher and we even tried it but stopped it thinking it wasn’t the one! That was bad!
And of course, we didn’t win the CTF just because of that damn cipher. What a shame right? That’s right, I was not really happy about it and I am a person who hates these kinds of challenges as they don’t really bring any value when thinking from a real-world security standpoint.
So I decided to solve this problem by writing a tool! As a very lazy person, I procrastinated a lot by not writing it and that’s when one of my friends suggested making a tool just for this! And that day, that literal day, I wrote the first version of BaseCrack!
In my opinion, the first version was kinda terrible as it only worked with Python2 and the CLI output was not that clean. But this version… It’s the BaseCrack I envisioned!
So what’s BaseCrack?

BaseCrack is a tool written in Python that can decode all alphanumeric base encoding schemes. This tool can accept single user input, multiple inputs from a file, input from an argument, multi-encoded bases, and decode them incredibly fast.
Link to the tool: GitHub.
It supports Base16, Base32, Base36, Base58, Base62, Base64, Base64Url, Base85, Base91, Base92 etc.
It’s useful for CTFs, Bug Bounty Hunting, and Cryptography.
Supported Encoding Schemes:
- Base16
- Base32
- Base36
- Base58
- Base62
- Base64
- Base64URL
- Base85
- Base91
- Base92
Features
- MAGIC MODE: Got a multi-encoded base? BaseCrack got you covered. Just give it the input and the rest is taken care of within milliseconds. It will identify the encoding scheme and unfold the encoded value with 0 false-positives! How? It’s explained below!
- Decode multiple base encodings from a file.
- Generate a wordlist/output with the decoded bases.
- Predicts the type of encoding scheme.
Installation
$ git clone https://github.com/mufeedvh/basecrack
$ cd basecrack/
$ pip install -r requirements.txt
$ python basecrack.py
And that’s literally it!
Usage
To decode a single base encoding from user input:
$ python basecrack.py
To decode a single base encoding from an argument (-b/–base):
$ python basecrack.py -b SGVsbG8gV29ybGQh
To decode multiple base encoding from a file (-f/–file):
$ python basecrack.py -f file.txt
MAGIC MODE: To decode multi-encoded base of any pattern (-m/–magic):
$ python basecrack.py –magic
To generate a wordlist/output with the decoded base (-o/–output):
$ python basecrack.py -f file.txt -o output.txt
API
Guess what? BaseCrack can be used as a library too! It comes in handy if you want to integrate BaseCrack into one of your projects or maybe your automation tool! 😉
It’s really simple, I will show you how! 🙂
Just put basecrack in your project’s folder and you’re ready to go!
Example:from basecrack import BaseCrack
result = BaseCrack().decode(‘c3BhZ2hldHRp’)
print(‘Decoded String: {}’.format(result[0]))
print(‘Encoding Scheme: {}’.format(result[1]))
Output:
Decoded String: spaghetti
Encoding Scheme: Base64
Screenshots
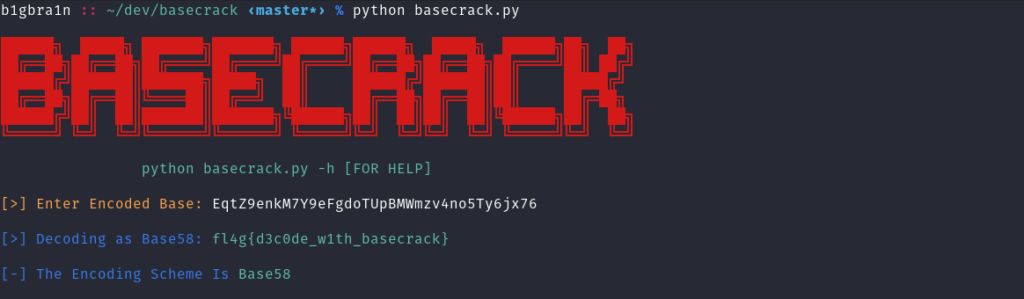
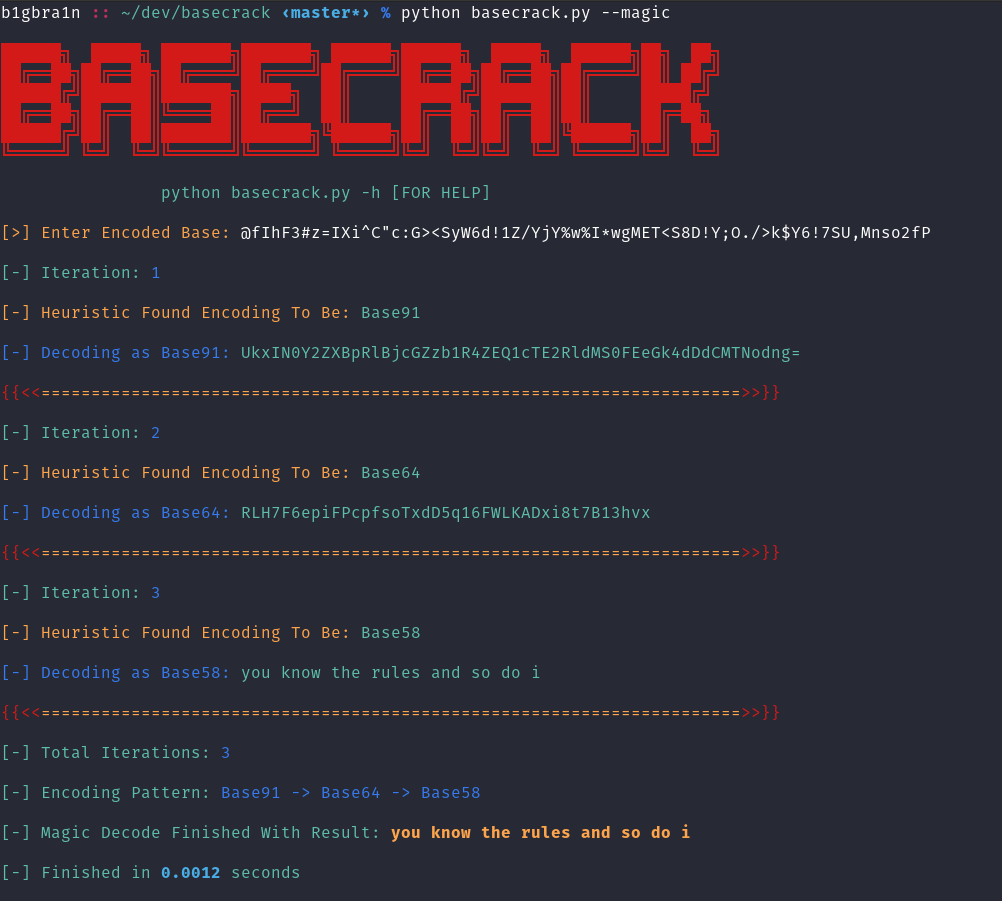
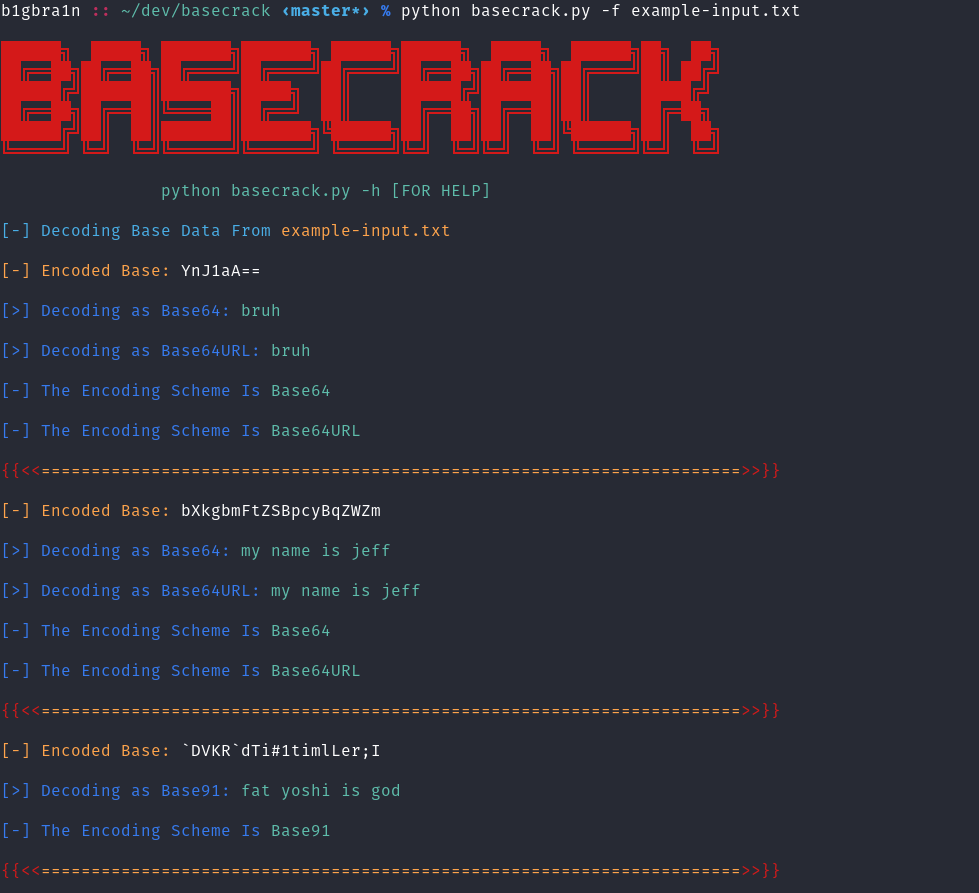
How does it work?
Let’s break it down to the problems we have to solve!
- Predicting the encoding scheme/type.
- Fastness in decoding multiple encodings.
- Deciding when to stop unwrapping or decoding a multi-encoded base.
I will cover all these questions with this one section!
Every encoding is different but some of them are easier to identify. For example, Base64 will have an equal sign (=) or double equal sign (==), but not every Base64 value has an equal sign! Umm, so what do we do? And also… there are multiple encoding types we have to predict!
So how did I solve it? Let’s take a look at how my lazy brain figured out a solution! 😅
What I noticed when making BaseCrack v1.0 was that, when we tried to decode a Base-X value with a Base-Y decoding function, it always had a “�” value which is the “replacement character” or U+FFD in Unicode. So why not check if the result of a decoding function contains this character and throw them out which will leave us with the accurate base encoding type!
All I had to was:def contains_replacement_char(res):
return True if u’\ufffd’ in res else False
2 lines and we solved the problem! But the only problem here is that we have to run through all the decoding functions which mess with the completion time but it only takes milliseconds to complete all of them so this solution is pretty good. The other way to do it will be by calculating the entropy of the encoded value which is apparently what CyberChef does!
So to the third question, how does it know when to stop decoding a multi-encoded base! What if we stopped when it’s a valid string or a word but what if the original value was gibberish or perhaps a CTF flag? Well, the above 2 lines can solve this too!
Just by decoding the value over and over until it contains the replacement character is enough to solve this issue because a value containing this character is not actually valid so we end up with the original value and the accurate encoding scheme!
Conclusion
This was a blog about how I came up with this idea and how I implemented it! I hope you will find this tool useful sometime in your infosec journey! 🙂
GitHub: https://github.com/mufeedvh/basecrack
If you liked it, give it a star, share it, and contributions are more than welcome!
See you guys in yet another YAS blog! 😉

Leave a Reply